Olá, pessoal!
Bom dia.
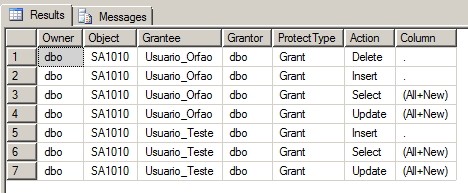
Neste post, irei demonstrar como verificar as permissões de um usuário e/ou database no SQL Server, além de permitir facilmente remover esses acessos ou conceder novamente. Caso você queira é replicar as permissões de um usuário entre instâncias diferentes, veja se o artigo SQL Server – Como copiar/replicar as permissões de um usuário pode te ajudar.
Utilizando a SP de sistema, sp_helprotect
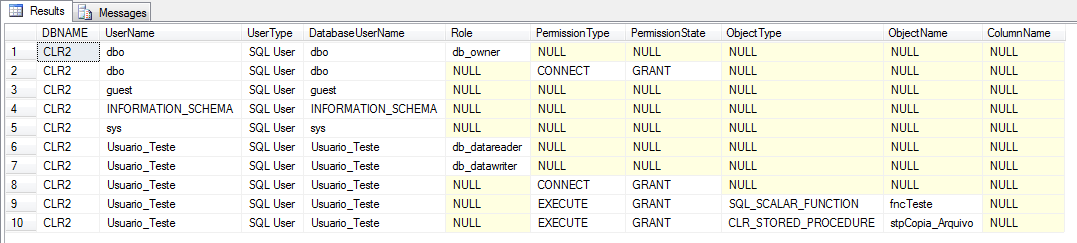
Através do uso da stored procedure sp_helprotect, podemos facilmente listar as permissões de um determinado usuário ou objeto:
|
1 2 3 |
-- Verificando as permissões do usuário "Usuario_Teste" EXEC Protheus_Producao.dbo.sp_helprotect @username = 'Usuario_Teste' |
|
1 2 3 |
-- Verificando as permissões da tabela "SA1010" EXEC Protheus_Producao.dbo.sp_helprotect @name = 'SA1010' |
Utilizando consultas Transact SQL em views de catálogo
Uma forma muito interessante de se obter e trabalhar com essas informações que vimos na interface do SQL Server Managment Studio é utilizando queries SQL e views de catálogo do banco de dados SQL Server. Essas queries trazem mais informações que a sp de sistema sp_helprotect e assim como utilizando a SP, podemos trabalhar com os dados retornados.
Visualizar código-fonteUtilizando uma Stored Procedure personalizada
Com um pouco mais de trabalho e refinamento, podemos utilizar uma Stored Procedure para essa finalidade. Podemos utilizar o retorno para gerar um relatório de acessos, gravar as informações para histórico, etc. Veja como é fácil:
Visualizar código-fonte da SPExemplos de utilização
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 |
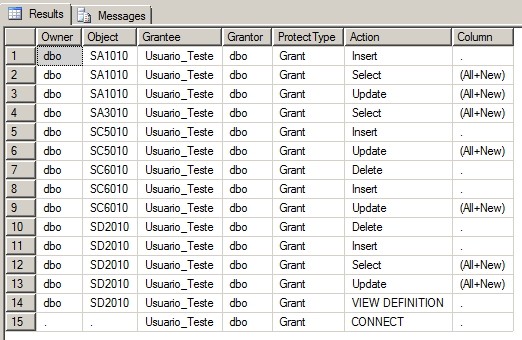
-- Verifica todas as permissões do usuário 'Usuario_Teste' na instância EXEC dbo.stpVerifica_Permissoes @Ds_Usuario = 'Usuario_Teste' -- Verifica todas as permissões da tabela 'SA1010' no database 'Protheus_Producao' EXEC dbo.stpVerifica_Permissoes @Ds_Database = 'Protheus_Producao', @Ds_Objeto = 'SA1010' -- Verifica as roles de database do usuário 'Usuario_Teste' em todos os bancos EXEC dbo.stpVerifica_Permissoes @Ds_Usuario = 'Usuario_Teste', -- varchar(100) @Ds_Database = NULL, -- varchar(100) @Ds_Objeto = NULL, @Nr_Tipo_Permissao = 1, @Fl_Permissoes_Servidor = 0 -- Não -- Verifica as permissões a nível de Database do usuário 'Usuario_Teste' EXEC dbo.stpVerifica_Permissoes @Ds_Usuario = 'Usuario_Teste', -- varchar(100) @Ds_Database = NULL, -- varchar(100) @Ds_Objeto = NULL, @Nr_Tipo_Permissao = 2, @Fl_Permissoes_Servidor = 0 -- Não -- Verifica as permissões do database 'Protheus_Producao' para todos os usuários EXEC dbo.stpVerifica_Permissoes @Ds_Usuario = NULL, -- varchar(100) @Ds_Database = 'Protheus_Producao', -- varchar(100) @Ds_Objeto = NULL, @Nr_Tipo_Permissao = 2, @Fl_Permissoes_Servidor = 0 -- Não -- Verifica as permissões a nível de sistema da instância EXEC dbo.stpVerifica_Permissoes @Nr_Tipo_Permissao = 4 -- Verifica os membros de roles de sistema da instância EXEC dbo.stpVerifica_Permissoes @Nr_Tipo_Permissao = 3 |
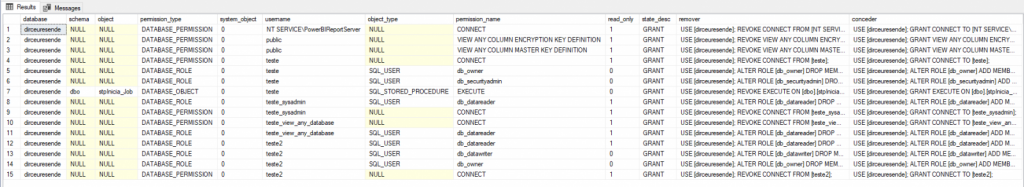
Exemplo de retorno (primeiro exemplo)
Utilizando uma Stored Procedure com código de GRANT e REVOKE
Assim como a Stored Procedure anterior, essa versão é um pouco mais “compacta” e ainda gera os códigos T-SQL para conceder esse privilégio existe (caso você queira fazer um backup das permissões existentes) e também o código T-SQL para remover essa permissão.
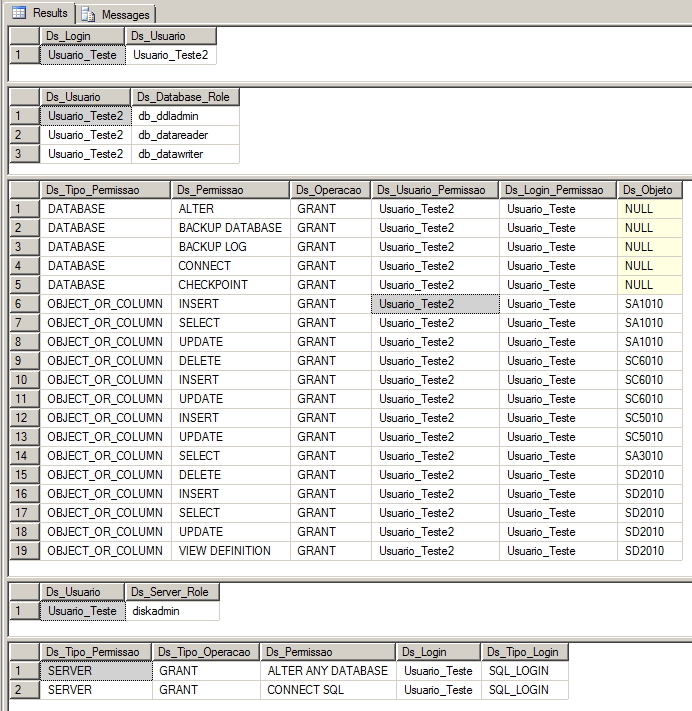
Visualizar código da stpVerifica_Permissoes_UsuarioExemplos de uso:
|
1 2 3 4 5 6 7 |
-- Verifica as permissões de todos os usuários do database "dirceuresende" EXEC dbo.stpVerifica_Permissoes_Usuario @Ds_Database = 'dirceuresende', -- varchar(50) @Ds_Usuario = '', -- varchar(50) @Fl_Objetos_Sistema = 0, -- bit @Fl_Permissoes_Instancia = 0, -- bit @Fl_Permissoes_Banco = 1 -- bit |
|
1 2 3 4 5 6 7 |
-- Verifica as permissões do usuário "teste" em todos os databases EXEC dbo.stpVerifica_Permissoes_Usuario @Ds_Database = NULL, -- varchar(50) @Ds_Usuario = 'teste', -- varchar(50) @Fl_Objetos_Sistema = 0, -- bit @Fl_Permissoes_Instancia = 0, -- bit @Fl_Permissoes_Banco = 1 -- bit |
|
1 2 3 4 5 6 7 |
-- Verifica todas as permissões dos usuários "%teste%" em todos os databases e a nível de instância EXEC dbo.stpVerifica_Permissoes_Usuario @Ds_Database = NULL, -- varchar(50) @Ds_Usuario = '%teste%', -- varchar(50) @Fl_Objetos_Sistema = 0, -- bit @Fl_Permissoes_Instancia = 1, -- bit @Fl_Permissoes_Banco = 1 -- bit |
|
1 2 3 4 5 6 7 |
-- Verifica todas as permissões, de todos os usuários da instância EXEC dbo.stpVerifica_Permissoes_Usuario @Ds_Database = NULL, -- varchar(50) @Ds_Usuario = NULL, -- varchar(50) @Fl_Objetos_Sistema = 1, -- bit @Fl_Permissoes_Instancia = 1, -- bit @Fl_Permissoes_Banco = 1 -- bit |
Utilizando uma Query
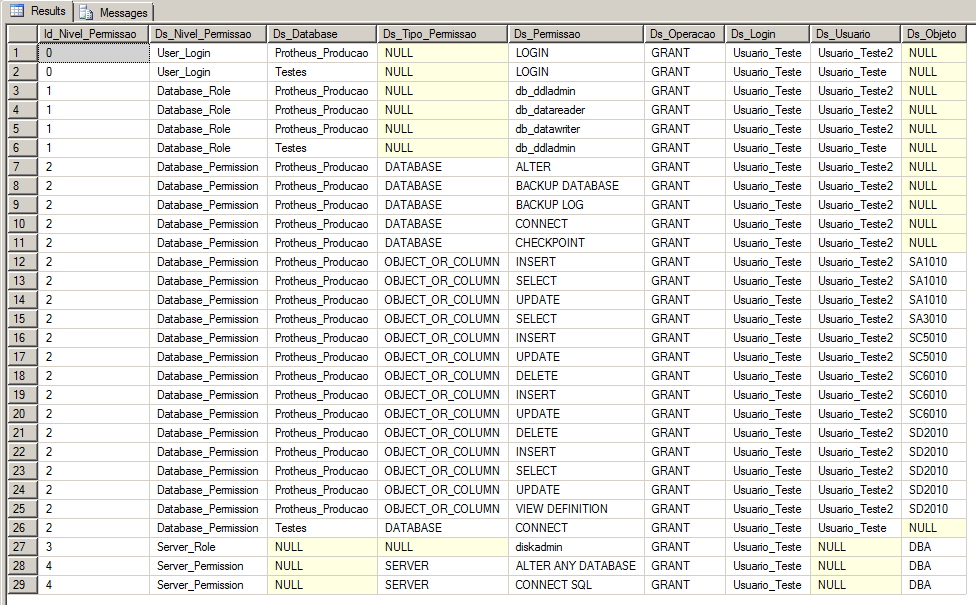
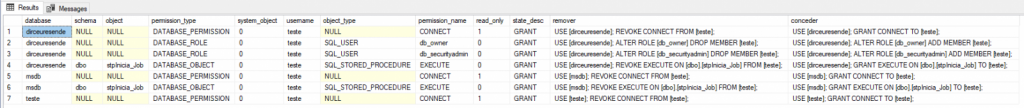
Uma outra alternativa rápida e prática para listar as permissões dos usuários é utilizando uma query com vários UNION para retornar as permissões a nível de role, sistema e objetos.
Visualizar código-fonte da queryUtilizando a interface (GUI) do SQL Server Managment Studio
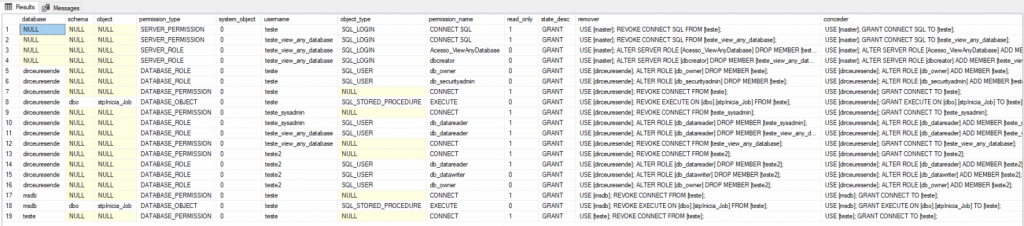
Uma forma bem fácil e prática para verificar as permissões dos usuários é utilizar a própria interface do SQL Server Managment Studio para isso. Na minha visão, o maior problema dessa solução é que você fica dependente da ferramenta e sabemos que um DBA não pode depender apenas de interface para o seu dia-a-dia. Outro problema que eu vejo nessa solução, é que você não consegue trabalhar com essas informações e utilizá-las para alguma rotina automática, por exemplo.
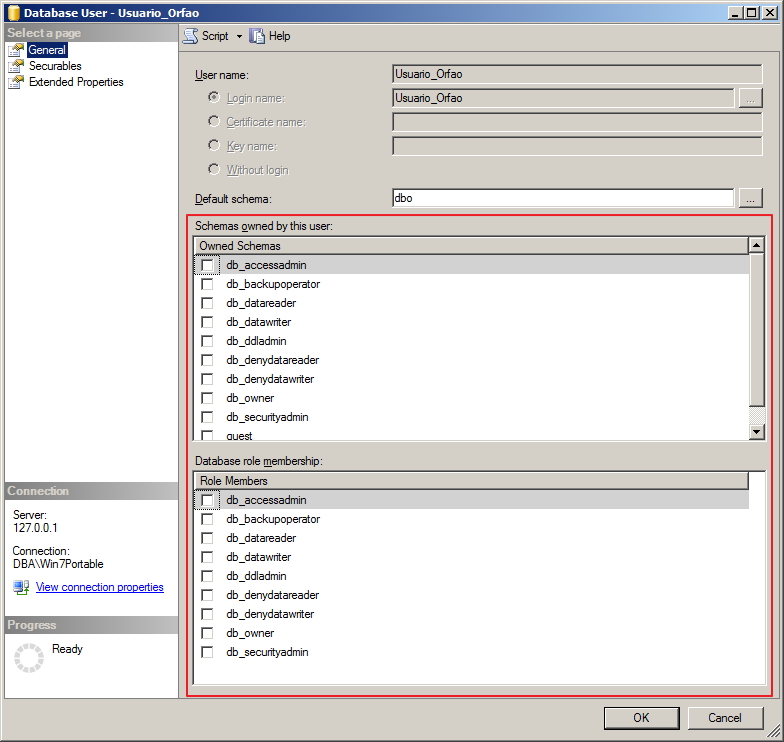
Nesta tela, podemos visualizar os schemas de propriedade do usuário e as roles a nível de database que esse usuário faz parte (Veja mais sobre database roles aqui).
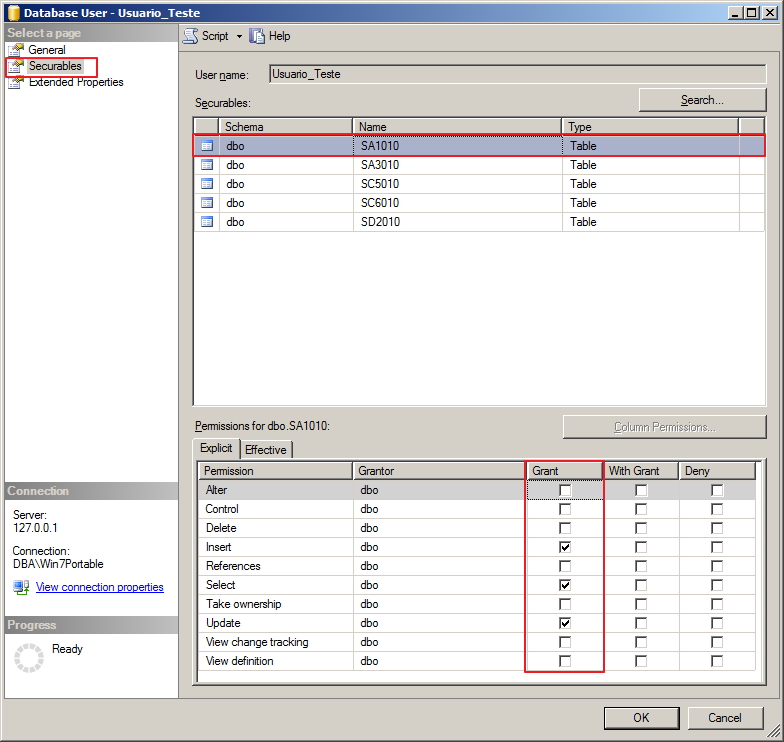
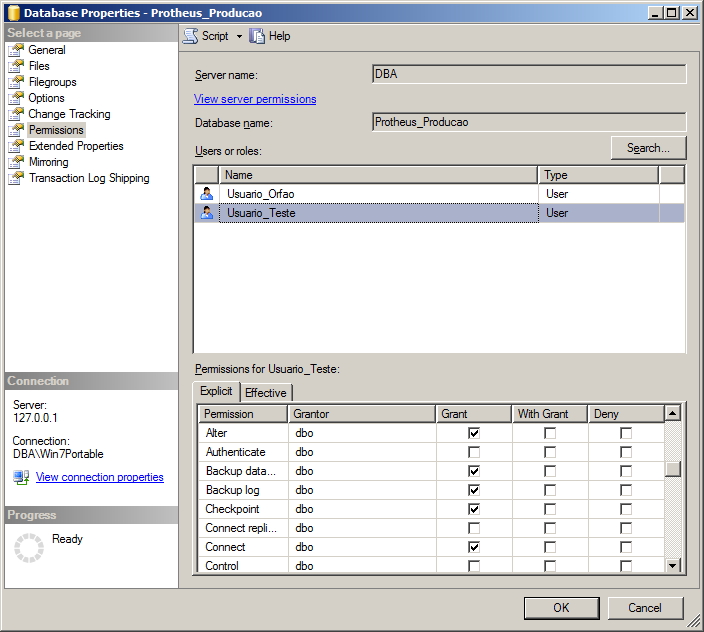
Nesta tela, podemos listar as permissões concedidas em cada objeto do database e por isso, temos essa visão por usuário e objeto.
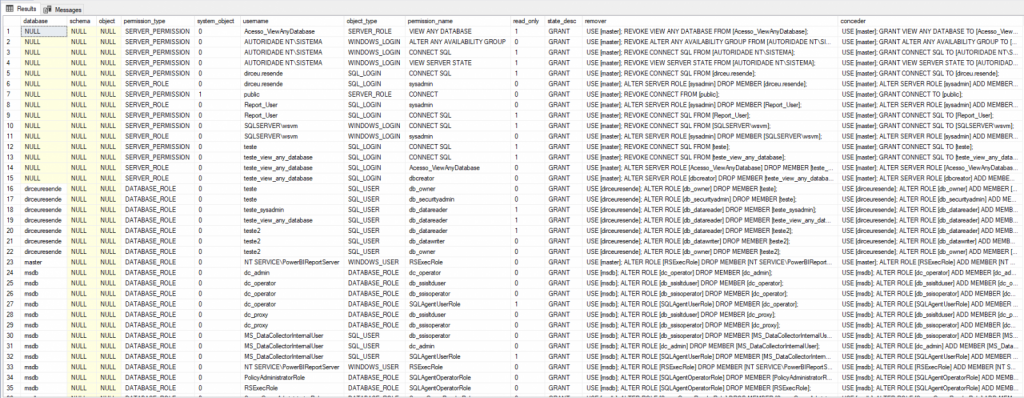
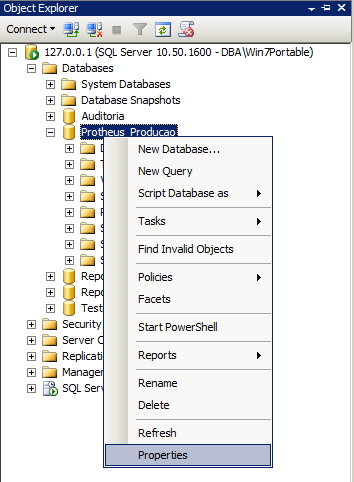
Permissões a nível de database:
Nesta tela, podemos definir as permissões a nível de database para um determinado usuário. Essas permissões se aplicam a todos os objetos desse database que esse privilégio engloba, além de permissões de manutenção no banco de dados (Ex: Backup, restore, checkpoint, etc)
Permissões a nível de servidor:
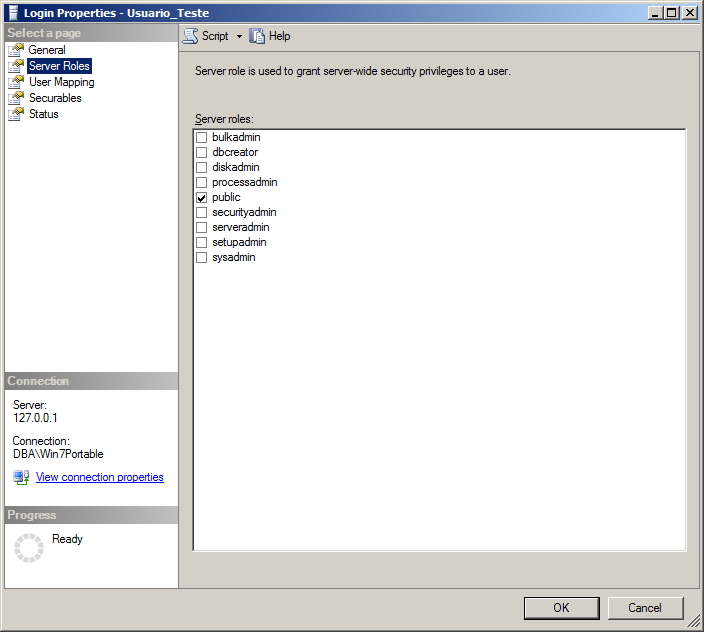
Permissões a nível de servidor – Server roles
Nesta tela, pode-se identificar quais roles a nível de servidor o usuário em questão faz parte. (veja mais sobre Server-side roles aqui)
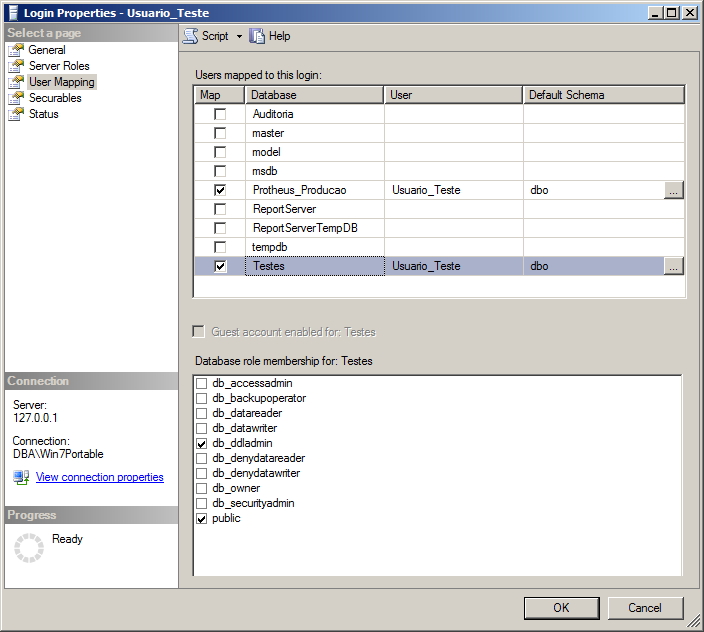
Permissões a nível de servidor – User Mapping
Nesta tela, você consegue identificar em quais databases um determinado Login possui usuário criado e quais roles a nível de database ele faz parte.
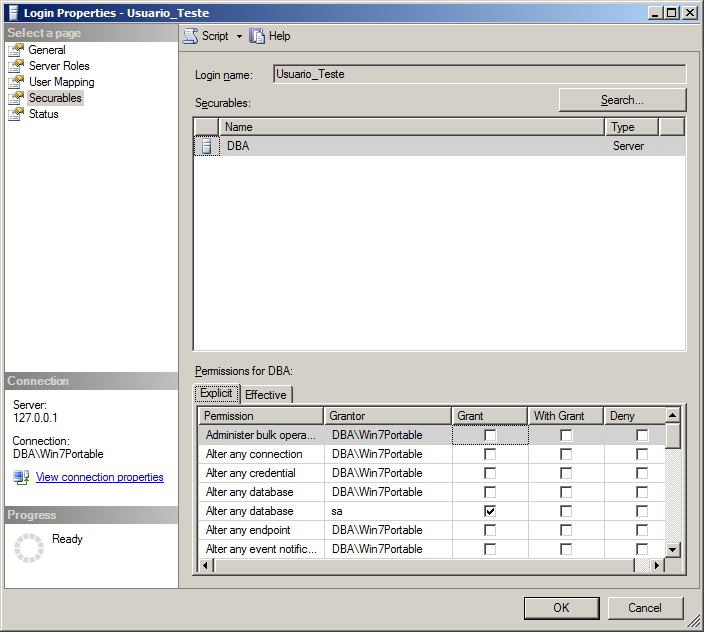
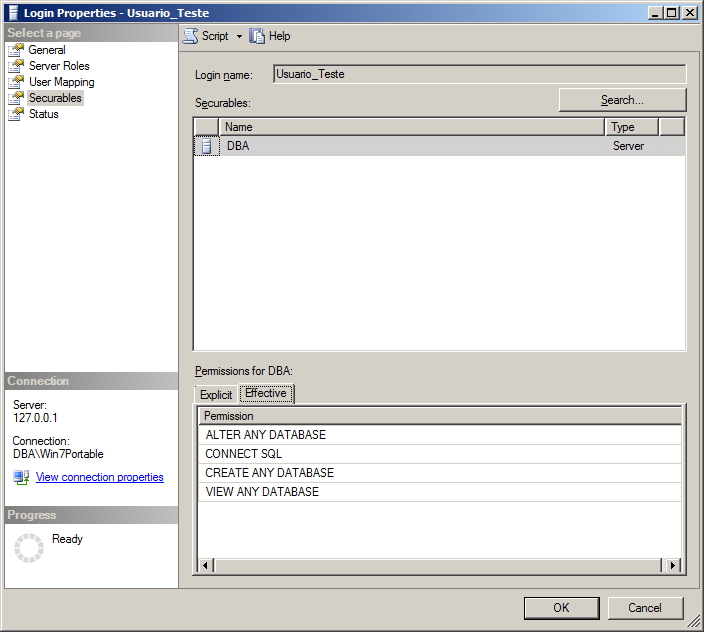
Permissões a nível de servidor – Securables
Nesta dela, podemos visualizar permissões em atividades de manutenção da instância, como Shutdown, Create any login, Create any database, etc..
And that's it, folks!
Espero que tenham gostado do post!
sql server list view report user system role object table view permission permissions listar visualizar relatório permissões acessos usuário usuários
sql server list view report user system role object table view permission permissions listar visualizar relatório permissões acessos usuário usuários


Ótima procedure! Muito útil!!!Só fiz uma alteração que não estava trazendo o nome dos schemas, mas agora vi que vc publicou uma versão já trazendo isso!!! Perfeita!
Otimo post..
Parabens.. Gostando muito do seu blog!
André,
Muito obrigado pelo feedback! Isso é muito importante.